Check Point Research
Researchers find security flaw in Rarible: Users could have lost all their NFTs
The research arm of cyber security software firm Check Point said it identified a vulnerability in the Rarible NFT marketplace that could have seen many of its roughly two million active monthly users lose their NFTs in a single transaction. Check Point is a multinational IT security firm that was founded in Ramat Gan, Israel in 1993 and also claimed to have spotted issues relating to malicious airdrops on OpenSea back in October 2021. According to documents shared with Cointelegraph, Check Point Research (CPR) recently discovered that malicious actors could send users a dubious link to an NFT that executes JavaScript code after clicking that “attempts to send a setApprovalForAll request to the victim.” If the link is clicked, the user grants full access to their wallets on Rarible. CPR st...
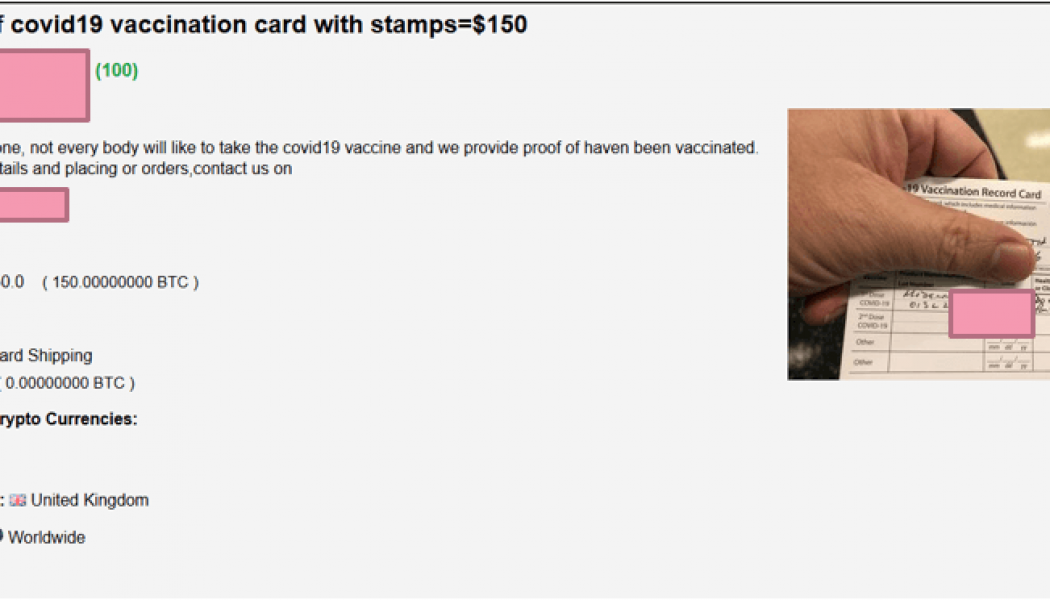
Fake COVID-19 Vaccination Certificates for Sale on the Dark Net
While the global roll-out of COVID-19 vaccinations continues to accelerate, it’s worth remembering that only around 1% of the world’s population have received their full course of injections. Billions are still waiting for their first dose, which inevitably leads those people to question exactly when they will get it. Especially as plans are being made internationally to allow those that have been vaccinated, or can prove they have had a recent negative test, the freedom to travel to other countries, attend large-scale events, take a new job, and more. So there’s a strong and growing demand for vaccinations and test results because of the greater freedoms they will give to people. And of course, there will always be people who don’t want to wait for their official vaccination, or for an of...
How COVID-19 could cause a Surge in QR Code Scams
Sourced from Forbes The COVID-19 pandemic has forced organisations all over the world to rethink the way they interact with their consumers. For instance, restaurants have opted to use QR codes so that customers can browse menus on their phone or make contactless payments without risking possible transmission. And now, Check Point is warning mobile users of the security risks of QR codes. The cybersecurity solutions company says that hackers are looking to take advantage of QR codes’ new popularity, by replacing legitimate QR codes with one that launches a malicious URL or tries to download customized malware. A recent survey by MobileIron showed that from March to September 2020, 38% of respondents scanned a QR code at a restaurant, bar or café, and 37% scanned a code at a retailer. Over ...
A Cyber Pandemic May Be Next: How Secure are you in the Cloud?
The Coronavirus pandemic has influenced us in a more global way than the Cold War, affecting the environment, industry, finance, healthcare, leisure and almost every other human endeavour. Some of the areas of influence are clear and obvious. For example, the acceleration of digital transformation, which changes how organisations operate and provide value to their customers. There is also an increased demand for cloud computing, which provides most of the foundations, tools and infrastructure to fuel the digital transformation. Some world leaders in the cybersecurity space, including the World Economic Forum, predict that this rapid and unplanned move will result in a cyber-pandemic down the road – more on that later. This acceleration in digital transformation and demand for clo...
Inadequate Investment in Cybersecurity is Behind Increase in Cyber Attacks
Following on this week’s Life Healthcare cyberattack, the issue of cybersecurity has once again been brought to the fore as businesses and individuals are forced to evaluate whether measures in place are strong enough to withstand major breaches in their security. Life Healthcare is the third major South African company that has been targeted by hackers this year. In February, Nedbank warned that the information of about 1.7 million clients was potentially affected by a data breach, and the following month chemicals and fertiliser maker Omnia Holdings said it’s IT infrastructure was subject to a cyberattack. Amongst the other big businesses that have been targeted in South Africa are Johannesburg City Council, Capitec Bank and Telkom. The trend is also true for the rest of the continent. I...
Check Point Software Partners Strathmore University to Promote Digital Skills in Kenya
Sourced from Business News Daily Cybersecurity solutions company, Check Point Software has announced that its education initiative has partnered with Strathmore University in Kenya to provide a comprehensive cybersecurity curriculum to students, bridging the digital skills gap and also creating a safer local cyber landscape. According to research, the number of unfilled cybersecurity roles now stands at 4.07 million professionals globally. What causes alarm for those within the security market across Africa is that the ICT courses across a range of disciplines are still underdeveloped, as well as the skills required to operate, support and understand the complexities of next-generation technologies and threats. Introducing the Check Point SecureAcademy To keep up with the current thr...