African Cybersecurity Landscape
Should West African Businesses Embrace Mobile Authentication for Security?
Sourced from International IDEA Digital technology has not only profoundly altered the way we live our lives, but also changed the pace of communication and commerce, allowing us to do everything, immediately. While this has effectively impacted every aspect of our lives, it also inevitably changed the way we are targeted by fraudsters. Along with the world transforming to digital, so has crime. According to an Accenture report published in 2019, the total value at risk of cybercrime over the next five years is an estimated $5.2 trillion. The average cyberattack costs $13 million, according to the same report, with phishing, social engineering and stolen device crime making up $2.4 million of the cost of an average attack. In West Africa, cybercrime is on the increase, with a recent analys...
Why People Should Invest in a Culture of Zero Trust Security
Sourced from International IDEA During a preview of this year’s RSA conference, a team from Orange Cyberdefense demonstrated a range of pretty scary scenarios of what can happen when malicious actors take control over a user’s home router. These range from duping users into downloading payloads dressed up as fake VPN software updates, capturing user’s credentials or redirecting traffic that should be going over the VPN to the threat actor. Typically, home routers are outside of the enterprise security control and often not very well protected. The majority of people trust their ISP to set up their home access points for them, frequently resulting in default settings such as admin/admin credentials. Home routers are frequently attacked by criminal and state actors alike. Despite the easing ...
Here’s How Many Mobile Users in Kenya and Nigeria are Affected by Stalkerware
Stalkerware affects one out of every 100 mobile users in Kenya and Nigeria, according to Kaspersky Research. The same report reveals that similar malware impacts every four out of 100 South Africans. “Even though these numbers might seem low, especially when it comes to stalkerware, it bears mentioning that this form of attack is focused on specific individuals,” says Lehan van den Heever, Enterprise Cyber Security Advisor for Kaspersky in Africa. “So, unlike general malware that is distributed on a massive scale, stalkerware is a more personal crime that has life and death consequences for the individual affected, for example, a perpetrator can track down their estranged partner with ill intentions, or human trafficking rings targeting children.” Amongst other things, stalkerware can enab...
Why Cybersecurity Patches are only Part of a Plan
Patches are undoubtedly an essential component of a cybersecurity strategy. They can be used to address vulnerabilities, resolve issues or improve solutions. However, a patchwork approach alone is simply no longer sufficient. The current digital landscape, with many employees continuing to work from home, means most organisations’ attack surfaces are so much wider and less contained than before. Businesses need a plan that includes patch management and vulnerability management as part of an overarching strategy aimed at mitigating and managing cybersecurity risk. A place for patches Patches are useful tools, ensuring that updates can be pushed out, vulnerabilities addressed and recommended configuration changes made across an organisation. Patches are typically a retrospective development ...
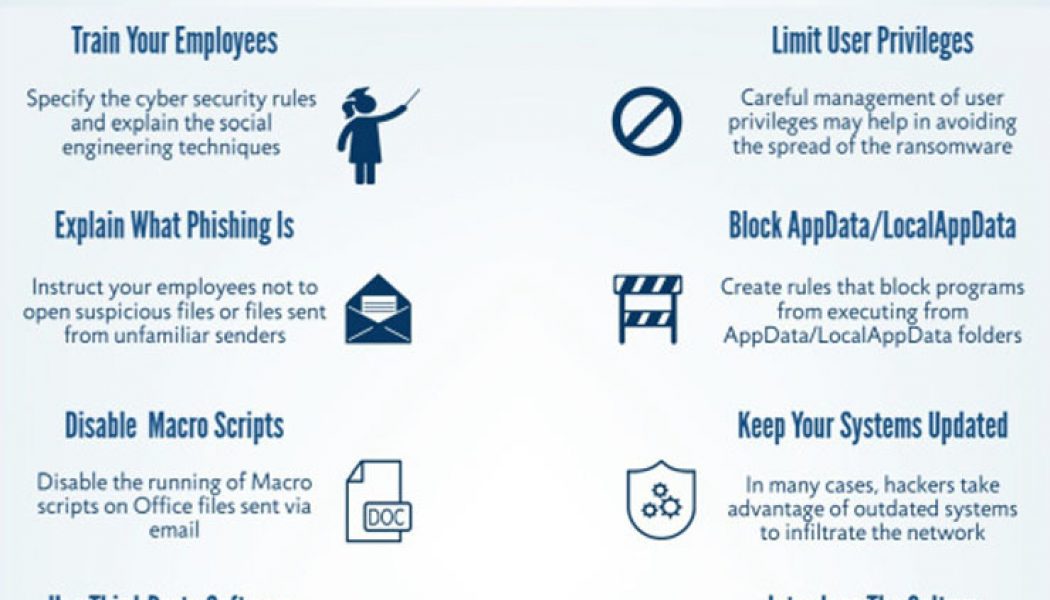
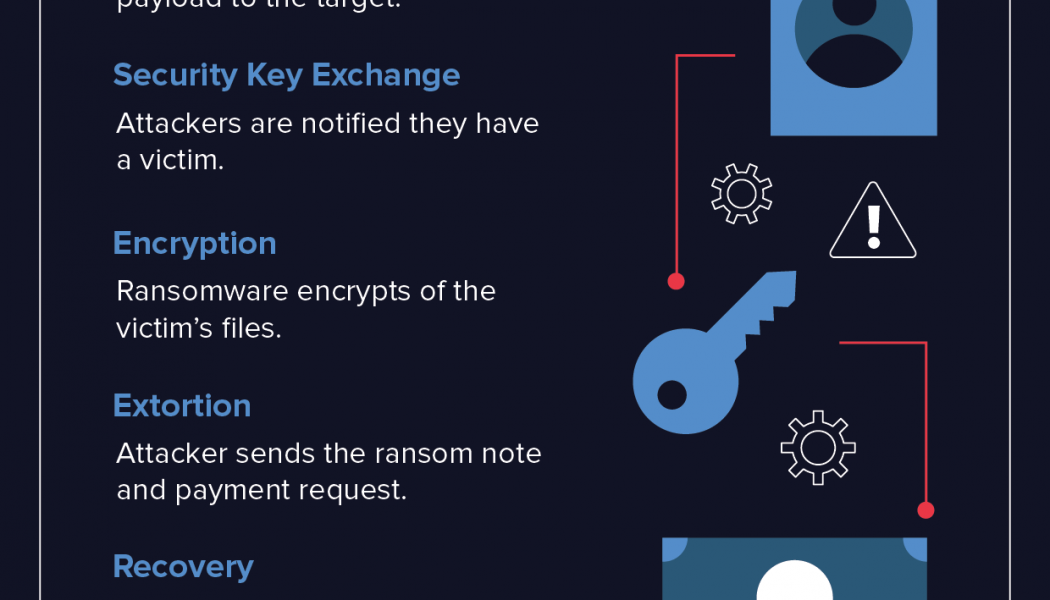
Research Shows an Increase in Ransomware Attacks on South African Companies
South Africa is firmly in the sights of international cybercrime syndicates, who have been ramping up their attacks on local companies in the past six months – reveals cybersecurity defence, offence and protection specialist, Nclose. Martin Potgieter, Co-Founder of Nclose, says the Nview MDR team have detected a significant uptick in the number of attempts made against local customers in recent months. “We, and our colleagues in the cybersecurity sector, are seeing a surge in cybercrime activity – in particular ransomware attacks,” he says. “There has definitely been an increase in syndicates that make use of humans to launch and coordinate their attacks, they are not just relying on automated ransomware attacks.” Stephen Osler, Co-Founder at Nclose, says South African companies typical...
Are University’s Doing Enough to Address the Cybersecurity Skills Gap
Sourced from International IDEA A global shortage of cybersecurity professionals has become so severe that companies are increasingly at risk from hacking and industrial espionage. Protecting data and defending corporate networks is poised to be one of the most in-demand careers of the future. Yet companies are already struggling to fill job vacancies, and the problem is accelerating. “Every company is going digital, and the first thing they have to ask is how secure are their networks and data,” says Doros Hadjizenonos, the Regional Sales Director at Fortinet. The danger is that cybercrime has grown so huge and lucrative that without enough good guys to keep them safe, businesses and individuals alike are in jeopardy. “If a company doesn’t have the right skills it’s increasing its risk to...
Protecting the IT Landscape in a Borderless World
The evolution of technology has pushed the perimeter of organisations further and further towards the edge, and we no longer have the monolithic structures we did in the past. The cloud, the Internet of Things (IoT), even the COVID-19 pandemic accelerating the adoption of a work from home model, have contributed to what has, in effect, become a borderless world. This means that the traditional approach to security of locking down the perimeter is simply no longer enough. The perimeter cannot be easily defined, and the way in which we access services has fundamentally changed. Cybersecurity mesh has emerged as a framework to address this challenge, with a distributed security architecture that more effectively meets the challenges of today’s landscape. Trust no one With IT infrastructure so...
Fixing Your Cybersecurity Issues 1 Next-Gen Firewall at a Time
Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited Africa When did you last check your firewalls as a barrier to entry against cybercriminals? And, perhaps more importantly: does your organisation still rely on a legacy firewall, or has it upgraded to a next-generation firewall (NGFW)? And have you considered the ‘Broken window’ principle when looking at your internal cybersecurity posture, in order to have a positive effect on your business processes? These questions are posed by Stefan van de Giessen: General Manager: Cybersecurity at Networks Unlimited Africa, who says, “The broken window theory rests on the idea that a neighbourhood or community that appears to be orderly and well-kept will be less susceptible to crime. Conversely, one that has many broken wind...
- 1
- 2