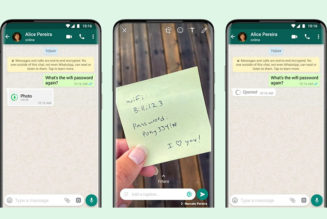
Many organisations across Africa are finding themselves transitioning their workforce to remote work at home as a result of the COVID-19 pandemic. IT departments are re-architecting their environments on the fly to allow for remote access.
Now, according to a report by Serianu, Pan-African based Cybersecurity and Business consulting firm, “in Nigeria, remote connections have increased by around 44% since the onset of COVID-19 with the highest increase realized in March 2020 after the president declared lockdown in key cities. Lagos is, by a vast amount, the most affected state, hosting over 40% of the identified vulnerable connections put at over 4,500 vulnerable connections.”
The Guardian Nigeria goes on to note that the report marks increased usage of these services causes an increased risk of compromise. Remote Desktop Protocol (RDP) and VPN services have registered a history of security issues and publicly disclosed vulnerabilities and many organisations are slow to patch their systems for known exploits.
William Makatiani, MD of Serianu, identifies how organisations can protect themselves.
/* custom css */
.tdi_3_eff.td-a-rec-img{ text-align: left; }.tdi_3_eff.td-a-rec-img img{ margin: 0 auto 0 0; }
He says “It is important to remember any time you try to access something remotely there is a risk. And because Remote Desktop Protocol fully controls a system, you should regulate, monitor and manage who has access closely. Enable strong passwords and account lockout policies to defend against brute-force attacks; use two-factor authentication; audit your network for systems using RDP for remote communication. Disable the service if unneeded or install available patches. Users may need to work with their technology vendors to confirm that patches will not affect system processes among others.”
Likewise responding to the report is Kenneth Okereafor, a cybersecurity and biometric expert, who says that COVID-19 pandemic has a peculiar impact on the state of cybersecurity in Africa, “peculiar due to our unique economic and developmental challenges. The social distancing requirements of the pandemic have necessitated the embrace of technology for remote office colloquially referred to as “Work From Home” since we live in a highly connected world of data”.
Okereafor identifies three distinct and important cybersecurity issues which organizations in Nigeria have to contend with as employees work from outside of a traditional office environment are.
“First,” he says is “sensitive official data being transmitted across unsafe telecommunications channels and poorly-protected telecommuting systems can be intercepted by internet fraudsters and used to defraud banks, gain unauthorized assess activate ransom advantage, or can be simply modified for use in future cybercrime.”
“As such, organisations must, therefore, ensure that their remote work communications channels including Wifi, radio, web portals etc, are protected with strong encryption technologies and intrusion detection systems.”
“Secondly, data leaks associated with insecure teleworking systems could become rampant due to poor access control mechanisms. The resulting privacy breaches have a long-term negative effect on the reputation of the organization and could trigger costly litigations, operational disruption, or negative impact on business survivability. As a remedy, prior to adopting remote work systems, corporate organizations must provide strong identity authentication systems to forestall impersonation and to enforce multi-layered verification of legitimate personnel authorized to access classified data.”
He says that with slow networks, remote work can quickly become a nightmare. Delayed access to data could impose life-threatening impacts on organizations that rely on the timeliness of data access for services such as banking transactions, emergency healthcare, aviation control, and criminal forensics.
What is required, Okereafor believes, is a holistic Coordinated Continental Cybersecurity Agenda (CCCA) to prevent, detect and mitigate the COVID-19 induced cybersecurity breaches is proposed, including benchmarking, idea sharing, cybersecurity legislation and attribution, capacity development, and technology transfer.
Edited by Luis Monzon
Follow Luis Monzon on Twitter
Follow IT News Africa on Twitter
/* custom css */
.tdi_4_5b5.td-a-rec-img{ text-align: left; }.tdi_4_5b5.td-a-rec-img img{ margin: 0 auto 0 0; }