Powered by the convergence of 5G and industry 4.0, the smart enterprise of the future is now here. The critical performance boost of 5G enables critical smart systems to share and respond to information faster than ever, permitting industrial enterprises to digitise and automate their infrastructures with confidence.
5G offers a unique and valuable set of capabilities that, unlike any previous or current mobile technology, enable and expand the implementation of transformative technologies for organisations, including industrial enterprises. The value of 5G encompasses enhanced bandwidth, ultra-high reliability, low latency, high positioning precision, and native support for machine communications that organisations across a wide range of verticals, including manufacturing, logistics, and utility companies, are looking to harness and accelerate their digital innovation efforts.
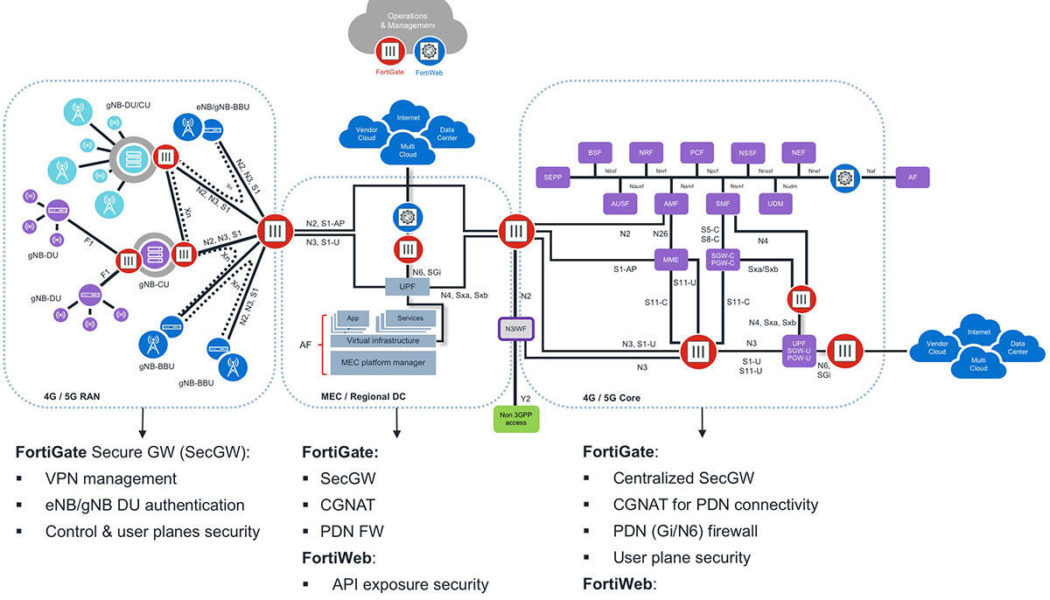
However, new technologies—especially those that add new edges to expand or enhance the potential attack surface—always bring new risks. As a critical part of an organisation’s businesses, 5G requires an end-to-end security infrastructure to ensure and maintain the secure deployment and utilisation of 5G across critical use cases such as augmented reality, autonomous-guided vehicles (AGVs), and near real-time digital twins, yielding innovative and increasingly efficient operations. Whatever version of 5G infrastructure and services is used, whether public or private, and whatever the implemented use case, however, security must be in place to help protect the attack surface across augmented 5G environments.
Understanding how an enterprise will use 5G, and how 5G mobile providers can best serve their needs, are essential for determining the security blueprint and related issues that must be addressed. However, it is also critical that organisations start this conversation on Day One of any transformation efforts by framing their security needs generally. Some of those main considerations are briefly discussed here.
Private 5G networks will be the go-to consumption choice for 5G enterprise
Research indicates that enterprises that consider deploying 5G will do so via nonpublic 5G networks (i.e., private 5G networks). This is supported by a near-continuous stream of industrial enterprises that have been announcing private 5G deployments. These deployments will be implemented by either mobile operators, mobile vendors, or systems integrators.
This is not a trivial undertaking. Deploying, maintaining, and managing a private 5G network requires significant financial and human resources. Customisation, QoS, SLA control, and system integrity (ensuring that production assets are protection in compliance with regulations) are the top factors driving these strategic and long-term investments.
The use case is king
Given the fanfare over the past few years, it would be easy to assume that the arrival of 5G is the culmination of everyone’s efforts. However, 5G is not the enterprise end game. 5G is simply a critical enabler for the real objective, which is the deployment and enablement of a great number of use cases that bring value and innovation to the enterprise. These may include such things as closed-loop process automation, real-time logistic management, augmented reality, predictive maintenance, and more. Delivery of such use cases requires the creation, deployment, and management of an interconnected 5G industrial ecosystem, including all related OT/IIoT devices and vendors, industrial applications and tools—both on-site and on public/partner clouds, and the 5G network itself.
It is the use case that needs to be secured, and meeting its unique issues and challenges should be the focus of any security infrastructure that is put in place. This is not a one-size-fits-all challenge, and we must not design or implement security in silos in such a complex ecosystem. Instead, we need to build and deliver end-to-end visibility, automation, and enforcement throughout the ecosystem’s attack surface as one coherent, integrated, adaptable, and self-healing security platform.
Native 5G security is not enough
We have all heard that 5G is the most secure commercial mobile generation and wireless technology ever developed, enhancing authentication, encryption, and integrity. But an internal 5G security mechanism is only part of the story. The 5G ecosystem that interlocks enterprises, providers, and partners serving their unique business interests creates a distributed attack surface that 5G on its own is unable to defend.
The rise of the sophisticated attacks—ranging from Advanced Swarm-Attacks that will leverage 5G-enabled devices to overwhelm defences, to increasingly sophisticated IoT/IIoT and API-based attacks that can leverage AI to speed delivery and outwit traditional and isolated security systems—warrants a defence-in-depth approach to security.
One that builds on the foundation of native 5G security with additional security layers to protect the entire 5G ecosystem end-to-end to deliver business-critical enterprise use cases.
By Muhammad Abid, Director of Product Management at Fortinet and Ronen Shpirer, Director of CSP Solutions at Fortinet