As we approach the two-year mark since the start of the COVID-19 pandemic, IT and security teams continue to grapple with massive changes it has wrought on enterprise networks. One of the biggest changes has been the need to support remote work, which initially was believed to be a temporary strategy necessary to keep businesses operational during the pandemic.
However, companies increasingly are realizing that remote work is here to stay. In fact, 87 percent of workers say they want to continue working remotely after the pandemic. And 42 percent of workers say they’ll look for jobs elsewhere if their current company doesn’t continue to offer long-term remote work options.
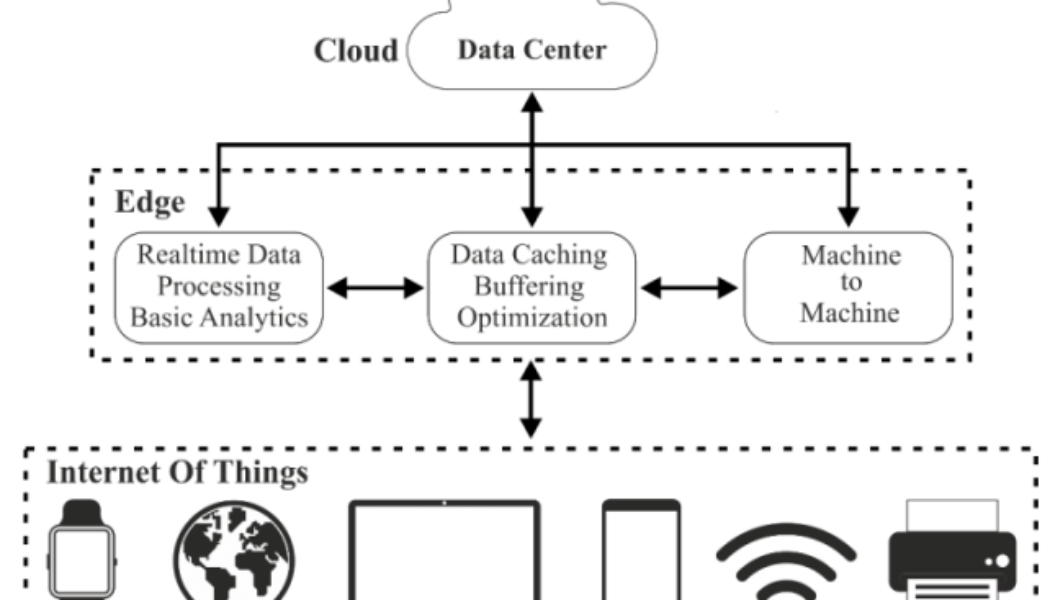
The need to support remote work and deal with other pandemic-related stresses has led many companies to embrace edge architecture, which enables processing and data storage to happen closer to the data source. Edge computing enables enterprises to increase network performance by reducing the need to send captured data from the network periphery back to a central system.
And there’s no question that enterprises want to glean the benefits of edge computing. In fact, more than half of all enterprises are expected to use edge computing for six or more use cases by the end of 2023. But as enterprises increasingly embrace the edge, cyberattackers are placing greater focus on it as well.
Although a great deal of attention has been focused on stopping distributed denial-of-service (DDoS) attacks at the edge, it’s also vitally important to focus on more granular application-layer DDoS. Application-layer DDoS attacks are primarily launched using discrete intelligent botnet nodes and target specific mechanisms to target application architecture and capacity. The result is that the attack renders the application incapable of delivering content to the user.
Three common application layer attacks illustrate their effectiveness:
- Slowlorisis an application layer DDoS attack that uses partial HTTP requests to open connections between a single computer and a targeted web server. The goal is to keep those connections open for as long as possible to overwhelm and slow the target.
- In aSlow Post DDoS attack, the attacker sends legitimate HTTP Post headers to a web server. In the headers, the sizes of the message body that will follow are correctly specified. However, the message body is sent at a painfully low speed—sometimes as slow as one byte every two minutes. Because the message is handled normally, the targeted server will do its best to follow specified protocol rules, resulting in the server subsequently slowing to a crawl.
- TCP state exhaustion attacksattempt to consume the connection state tables that are present in many infrastructure components, including load balancers, firewalls, and application servers themselves. Even high-capacity devices capable of maintaining state on millions of connections can be taken down by these attacks.
These attacks are made more insidious by the fact that attackers use them to monitor the results of their efforts. When vulnerabilities are found, the attacker modifies the attack to overcome the network’s defenses. Successfully detecting and stopping application layer attacks requires intelligent DDoS attack protection at the network edge to maintain the availability of business-critical applications.
Staff writer









Tagged: Security, Sponsored, Top Stories