Google said in a new blog post that hackers linked to the Chinese government have been impersonating antivirus software McAfee to try to infect victims’ machines with malware. And, Google says, the hackers appear to be the same group that unsuccessfully targeted the presidential campaign of former Vice President Joe Biden with a phishing attack earlier this year. A similar group of hackers based in Iran had tried to target President Trump’s campaign, but also was unsuccessful.
The group, which Google refers to as APT 31 (short for Advanced Persistent Threat), would email links to users which would download malware hosted on GitHub, allowing the attacker to upload and download files and execute commands. Since the group used services like GitHub and Dropbox to carry out the attacks, it made it more difficult to track them.
“Every malicious piece of this attack was hosted on legitimate services, making it harder for defenders to rely on network signals for detection,” the head of Google’s Threat Analysis Group Shane Huntley wrote in the blog post.
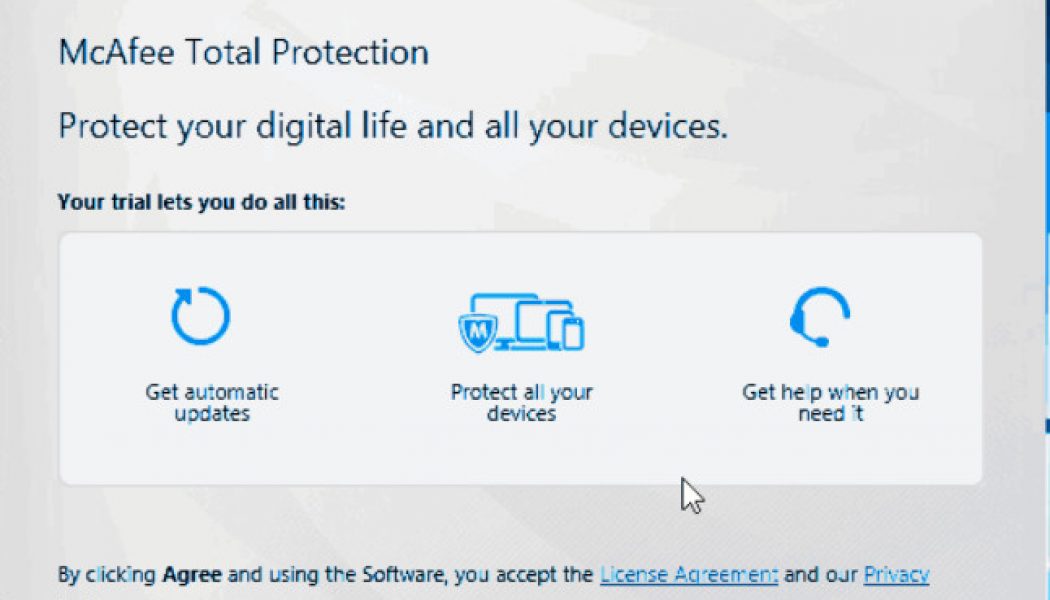
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/21968881/mcafee_attack.png)
In the McAfee impersonation scam, the recipient of the email would be prompted to install a legitimate version of McAfee software from GitHub, while at the same time malware was installed without the user being aware. Huntley noted that whenever Google detects that a user has been the victim of a government-backed attack, it sends them a warning.
The blog post doesn’t mention who was affected by APT-31’s latest attacks, but said there had been “increased attention on the threats posed by APTs in the context of the U.S. election.” Google shared its findings with the FBI.