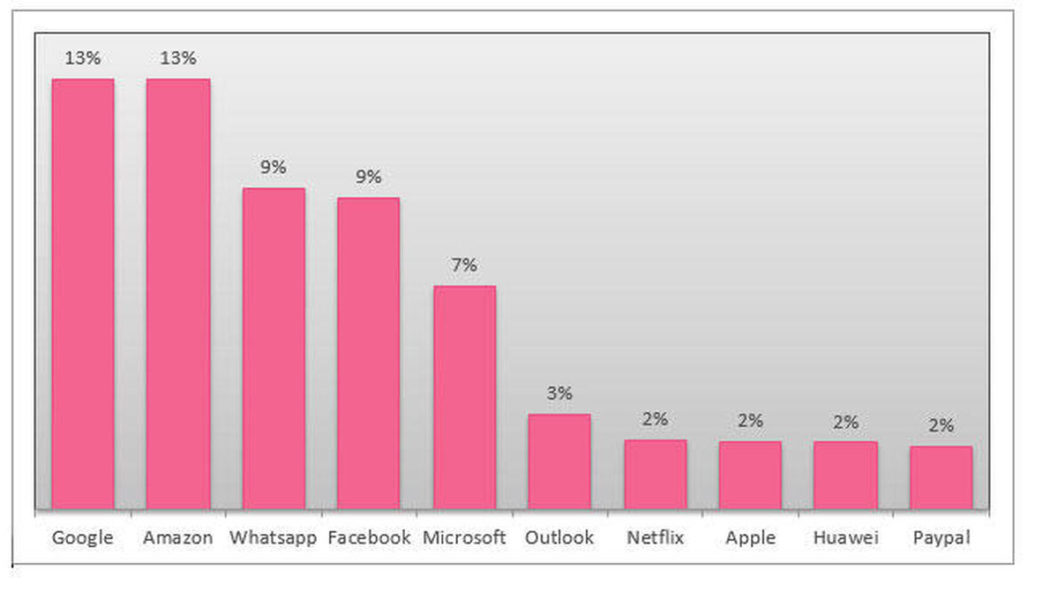
Check Point Research for the second quarter of 2021 found that Microsoft was the most popular brand used to lure unsuspecting individuals and employees.
This isn’t hard to believe because Microsoft’s Active Directory, continues to dominate the market share globally in 2021 and as a result is still the most popular target for phishing. The weight of this risk is emphasised by the fact that in 2021, phishing attacks increased by 47% in just the first quarter alone.
The threats are smart, capable, and worrying – increasing in volume every year. Companies are facing an onslaught of risk that’s designed to fool employees into making mistakes that can cost the company money and reputation.
“The risk is when employee credentials are stolen, this can lead to detrimental consequences for a business, even if these credentials are not privileged,” says Martin Potgieter, Co-Founder & Technical Director at Nclose.
“It’s that many companies have moved their compute services online over the past 18 months, many taking the digital plunge into the depths of Microsoft Office 365. This move brings extensive online collaboration and functionality, perfect for the remote workforce, but it also introduces a measure of unexpected risk.”
For Potgieter, the first challenge is to adapt mindsets and security approaches around access to Microsoft Office 365. The platform allows for users to log in from anywhere, at any time which is fantastic news for people who want to work from anywhere. However, the risk associated with this is an added attack surface, meaning an attacker has more entry points to use employee credentials– in turn, businesses can become lacklustre in dealing with this. These credentials are a hot commodity for cybercriminals hunting for a way into an organisation.
Microsoft is aware of the issue and is quick to notify customers and security teams of potential issues, most recently warning of a phishing campaign released by Russian group Nobelium. Another campaign, highlighted by Check Point, used a malicious phishing email designed to scare people into clicking on a fake link that took them to a fake Microsoft login page. Once users clicked on the link and entered their details, the information was logged, and the vulnerability door opened nice and wide for the attackers.
This evidence is further acknowledged by Potgieter who states, “Our Nview MDR service continues to see Microsoft phishing as the most common attack. Once the attacker has these credentials, they can do all kinds of things inside the business. All the attackers need is employee credentials, and with the added attack surface of remote working, these attackers can access all different kinds of company data without being noticed. Now that the world has become a giant office that allows working from anywhere, it’s equally become a giant cyberattack marketplace, allowing for threat actors to enter into companies from anywhere.”
Potgieter believes that one of the reasons why Microsoft Office 365 is so easy to phish is because it’s a victim of its own success – being the number one subscription service for businesses to use – in conjunction with being so popular, users are not protected by a dedicated VPN to access 365, so businesses have no way of differentiating between employee and attacker.
This means that – to a large degree – authentication is now exposed to the internet and if a user is tricked into handing over their credentials, this makes it easier for attackers to use those credentials for their benefit.
It’s also far easier to trick people than in the past,” says Potgieter. “Criminals can make a malicious web page look exactly like an authentic Office 365 SharePoint login and then automate the credential harvesting”.
Once the details have been entered into this fake page, the credentials are taken and either used by the attacker to perpetrate an attack or sold for the highest bidder. There are numerous cybercriminals that specialise in selling credentials.”
Mitigating this risk must become a priority for the organisation. This starts with the most basic step – training – and ensuring that users are constantly given the tools they need to identify most of the risks that can crop up online.
However, this needs to be bolstered by multi-factor authentication (MFA). This has become as important as a firewall and as basic a first step in embedding organisational security.
“If you don’t have a firewall, you’re at risk, and the same rule applies to MFA – this should be a basic part of the user online journey as not using a password like 12345,” adds Potgieter.
“If employees can identify a phishing email, or recognise one that may be a risk, then they are better prepared for the challenges in this landscape. So, ensure that people are trained, that MFA forms a basic part of any security posture, and invest into security that evolves with your remote and engaged workforce.”
Edited by Luis Monzon
Follow Luis Monzon on Twitter
Follow IT News Africa on Twitter