The cloud can enable organisations to quickly scale out enhanced security to a suddenly remote workforce, as part of efforts to ensure business continuity and disaster recovery – this is according to Patrick Grillo, Senior Director and Solutions Marketing at Fortinet.
The pandemic had created unique challenges for employers and employees across all sectors around the world, with Varun Kukreja, Senior Program Manager – IT Security MEA, IDC Middle East, Africa, & Turkey, saying securing the teleworker had become a top priority, with some 90% of organisations looking to provide staff with secure access to IT services and applications.
The pandemic had also accelerated digital transformation, he says, with an IDC Meta survey interim results revealing that some 56% of organisations scaling up their online presence to generate DX-led revenue streams and roughly 30% of CIOs and decision-makers set to spend more on public cloud services.
Grillo noted that remote working was not a new requirement, but says what was new was having to suddenly move entire workforces to remote work.
“The questions organisations should be asking themselves at times like these are: Is it a one size fits all scenario? Can I leverage existing resources? How secure is secure? And how can I scale to meet demand?” he says.
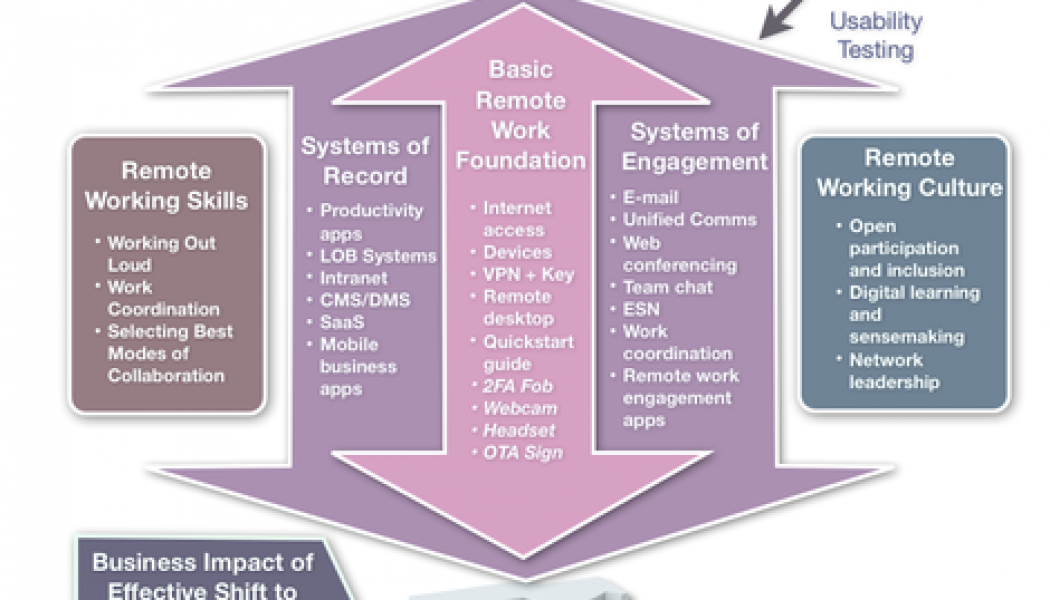
Grillo says that a newly-remote workforce might require different levels of security. “The general user might need only a laptop, with approved endpoint protection of the device, and two-factor authentication capability to access applications. Some of these users’ traffic is going to be directed at the corporate entity through the VPN tunnel. But if they need to go to a staff application, we want to avoid them having to go back to the corporate entity and then to the cloud. Split tunnelling, allowing me locally to segregate my traffic, some of it going to the corporate network and some directly to the internet where needed, will fit the vast majority of users.”
However, some users may require more capabilities, he says.
“For power users – those who need increased capability – we can extend the access layer, to bring that access layer out to where the power user is located. That means deploying a wireless access point at the user’s location and then having a VPN tunnel back into the corporate network. This is a much greater replication of somebody being in their native work environment than just dialling in from a remote location. We can take that one step further and go to the super-user, and rather than just extending the access layer, we’re actually creating a branch office at their location. In this case, we’re putting a networking security device at that location and for all intents and purposes, it’s as if they are in the office. They are attached to the main part of the network, it’s transparent, and you support greater capabilities.”
“But what about the head end? The organisation needs some capability to terminate all those VPN tunnels coming in from all those remote users, power users and super users. Aside from that, they must manage the endpoint protection plan which is now multiplied to a high degree. The management of that configuration now becomes more complex, so you going to have some sort of management system. Organisations will also need an authentication system which is also ideally capable of dealing with two-factor authentication and single sign-on. Ideally, they already have these capabilities, and to extend them, they can leverage the cloud. They don’t automatically need to buy more equipment.”
Grillo states “Leveraging cloud and cloud resources allow organisations to ramp up remote access capabilities, make sure there’s security in these connections, take advantage of virtual machines and deploy them in the cloud and in a matter of days, rather than weeks.”
Edited by Luis Monzon
Follow Luis Monzon on Twitter
Follow IT News Africa on Twitter