When COVID-19 closed offices worldwide, it created a new urgency for organisations of all kinds and sizes — and particularly the CIOs, CISOs and IT leaders within them — to secure their remote work environments.
As the need for remote work grew, so too did the threat landscape. For companies not born in the digital age, it was overwhelming to juggle their first cloud migration while conjuring overnight a new kind of security posture that met internet-scale levels of trust and performance. Where those businesses left gaps, often as a result of human error, cybercriminals were happy to exploit them.
As we enter the next phase, one where “work-from-anywhere” environments are here to stay, let’s rewind, pause and remember that the secret to success is to do common things uncommonly well.
Like washing your hands or wearing a mask during a pandemic, nailing the basics to promote cybersecurity hygiene can go a long way toward eliminating the risk associated with common cybersecurity threats.
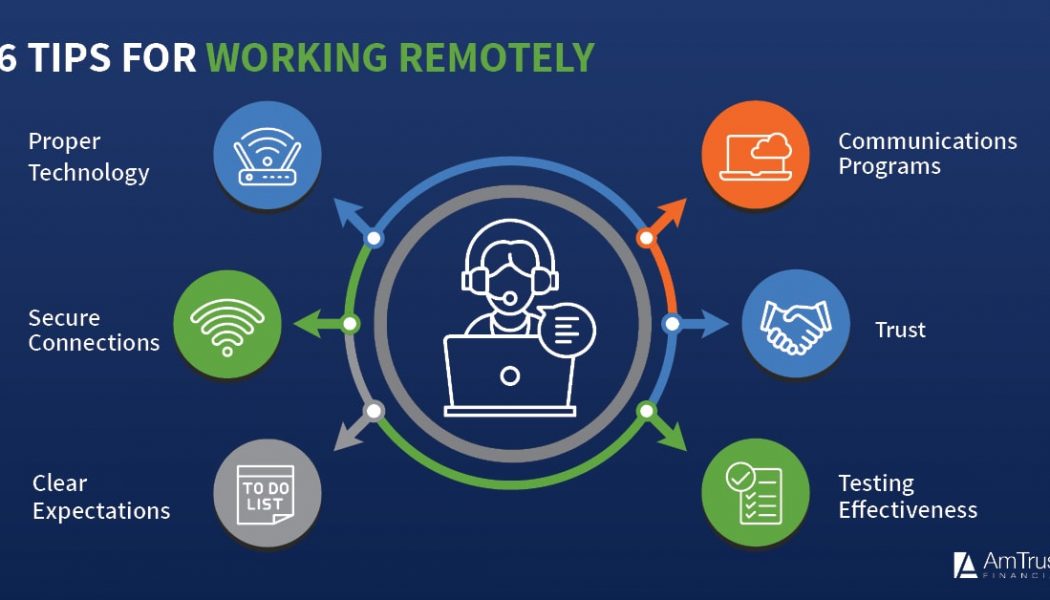
Whether you’re a veteran of securing remote work environments or just getting started, here are five important steps you can take to protect employee and customer data:
1. Enable Multi-Factor Authentication (MFA)
Passwords alone aren’t enough to protect against common security attacks. Weak or reused passwords are often the weakest link attackers love to exploit. As the security landscape evolves, multi-factor authentication (MFA) has emerged as one of the best ways to protect business and customer data.
By requiring users to enter two or more “factors” to prove their identity during the login process, MFA can drastically reduce the odds of unauthorised access even if a user’s password is stolen.
As your cloud migration picks up steam, enabling MFA as part of a defence-in-depth strategy instead of relying on employees to brainstorm unbreakable passwords and keep them safe can be a key success factor.
2. Patch your devices
Patching corporate devices is a simple, effective and direct way of ensuring employees inoculate themselves against known vulnerabilities, resulting in much-improved resilience against common attack vectors like ransomware.
Through patching, corporate devices also automatically add necessary new features, remove outdated ones and fix performance issues. Encourage your employees to patch their personal devices as well.
3. Beware of COVID-19 phishing emails
While phishing (and its cousin, vishing) scams are nothing new, the COVID-19 crisis has emboldened cybercriminals to steal personal information by taking advantage of confusion surrounding the rollout of financial assistance and other government programs.
As everyday citizens continue to fall victim to these scams, the companies they work for are increasingly affected —either through the loss of productivity or, even worse, stolen business data.
Here, again, is an example of how nailing the basics can go a long way, and it starts at the top. If CISOs and IT leaders simply raise awareness within their companies of these threats and how to spot them, security-aware employees can render phishing emails and vishing calls ineffective by looking for red flags, including:
-
Is the subject line off?
-
Is the email from a known person or organisation?
-
Is there anything suspicious about the attachment?
-
Is there something “phishy” about the credentials requested?
-
Is the email poorly written?
-
Is the message requesting immediate, urgent attention or money?
-
Is the call from a familiar phone number?
4. Secure your connection through VPN
Laptops, phones and, yes, even your smartwatch connect to the internet with varying (and sometimes random) levels of security controls. By requiring remote employees to use a virtual private network (VPN) on devices with access to business data, companies can dictate the terms of engagement when sending or receiving sensitive information through otherwise public connections.
Put another way: If transporting a briefcase full of cash, would you want a courier driving with the top down and $100 bills flying all over the interstate, or would you prefer a secret, secure tunnel purpose-built to keep intruders out? A VPN can give you just that.
5. Secure your meetings
With video conferencing at an all-time high, it’s more important than ever to review the security settings within your web conference platform of choice. For example, using a platform’s built-in security features — such as meeting rooms, passwords and screen-sharing permissions — can be basic but critical steps to managing activity and preventing unauthorised access to meetings.
Where possible, use unique passcodes and access links for meetings and disable “beta” features you don’t need like file-sharing or live streaming to minimise human error.
By Jim Alkove, Chief Trust Officer at Salesforce