Modernising business infrastructure by migrating to the cloud has become one of the most significant organisational priorities today. Unfortunately, as companies across industry sectors make the shift from on-premises to this dynamic new environment, so too has there been a tremendous increase in cyber threats and attacks. Contrary to the widely held belief, cloud computing is not the panacea for security many make it out to be.
The most effective cyber attackers target the weakest points in any company’s digital defences. In fact, there has been a 50% surge in more sophisticated cyberattacks over the past year. This can at least partly be attributed to the rate at which new cloud deployments are taking place which makes it difficult for business and technology leaders to keep up and ensure their systems are protected. Even though cloud service providers offer native security capabilities or third-party security vendors offer specific solutions, disparate approaches to security present new risks, complexity, and reduced visibility which complicates cloud security management.
1. Beyond cloud standard security
Cloud service providers only secure the infrastructure layer. It is still up to the organisation to make the transition to protect its data and apps in the cloud as well as safeguard how the information is transferred.
One of the most significant risks when it comes to companies adopting the cloud is the high likelihood of them misconfiguring their cloud security settings. This may lead to attacks such as privilege escalation from an external threat actor or even an insider. The global shortage of cloud security experts and a lack of complete visibility into infrastructure security, a limited understanding of how to set security policies, and figuring out how to best ensure both international and local compliance requirements are met add to the complexity of the environment.
Traditionally, those companies who had on-premises servers or private cloud focused on investing in securing their perimeter. However, the move to the public cloud requires a significant review of how best to manage security across multiple environments. But regardless of on-premises, public, private, hybrid, or multi-cloud environments, the perimeter must remain the primary focus of determining the ideal approach to cybersecurity.
2. Thinking differently
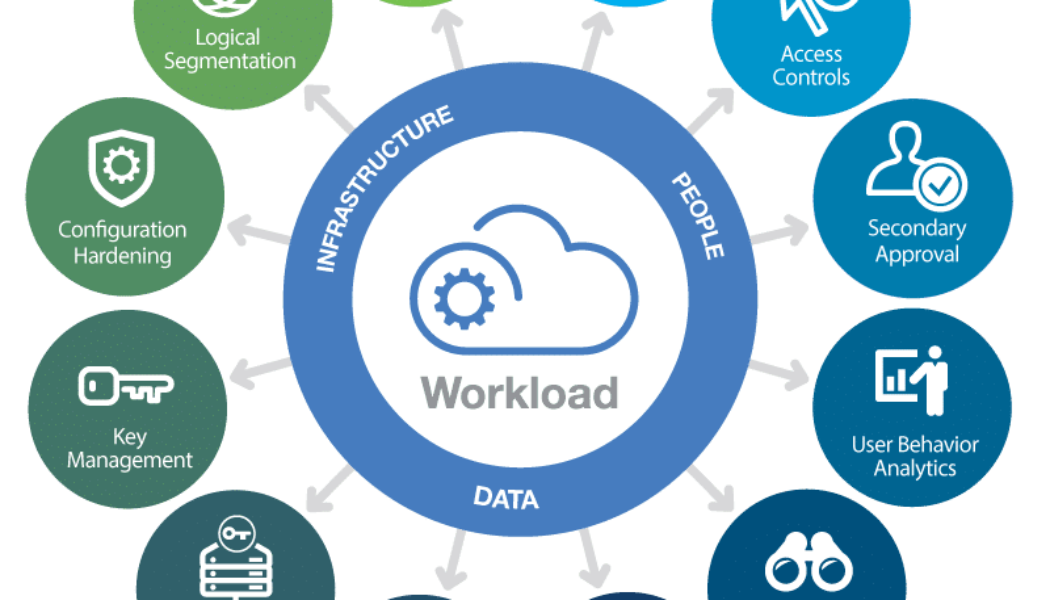
One of the ideal ways of securing the cloud assets of a business with ‘guardrails’ in place is having an automated, multi-layered security platform like Check Point CloudGuard. This must be designed to deliver advanced threat prevention and have the capabilities to automatically adapt and grow along with the business processes and strategies. Think of it as injecting scalability into cybersecurity real estate.
With this comes the ability to operate as a fully cloud-centric native security service with the highest level of threat intelligence and data enrichment capabilities. This ensures the company can effectively hunt and prevent external and internal threats across all perimeters.
More than that, the solution will allow the organisation to secure the higher layers of the cloud environment (think the network layer up to the application layer) with advanced multi-layer security. This provides the visibility into traffic and threats essential to help detect and prevent attacks inside and outside the cloud network and demonstrate compliance.
Additionally, a perimeter-based security gateway approach makes it easier to protect multiple virtual machine instances in a highly dynamic cloud environment where these are constantly spun up and removed.
3. Going agile
Ultimately, the cloud security of a business must be consolidated, automated, and as agile and adaptive as its infrastructural and architectural changes. Moreover, it must also integrate with the cloud-native security layers and give the visibility and monitoring capabilities essential to meet all compliance and security-related requirements.
Cloud-native multi-layer protection delivers zero trust and advanced threat prevention with workload protection that includes security hardening, runtime code analysis, Web, and API security. A unified security architecture provides intelligent threat prevention and gives decision-makers the toolsets essential to evaluate security posture, configuration guidance, alerts, and governance.
Having this full visibility of all its cloud assets and compliance footprint as well as control of the security posture on the public cloud to detect unauthorized access, misconfigurations, and unwanted data exposure, ensure organisations can future-proof their security posture. And it is this that will help define how successful a business will be at a time where digital-centricity, cloud adoption, and scaling to meet any customer requirement will be mission-critical competitive advantages.
By Lindsay Blackie, Channel Manager Check Point at Westcon-Comstor








Tagged: Cloud Computing, cloud security, Cloud security settings, cloud service providers, Cloud services, cyber attacks, cyber-threats, cybersecurity, data protection, Internal threat, IT, IT News, Lists, Multi-cloud environments, private cloud, public cloud, Security, security policies, Tech, tech news, technology, Third-party security